More than you might think, AI (Artificial Intelligence) and ML (Machine Learning) bots are crawling your site and scraping your content. They are collecting and using your data to train software like ChatGPT, OpenAI, DeepSeek, and thousands of other AI creations. Whether you or anyone approves of all this is not my concern for this post. The focus of this post is aimed at website owners who want to stop AI bots from crawling their web pages, as much as […] Continue reading »

Good news! The 8G Firewall is updated to version 1.4. This latest update resolves numerous false positives and bugs that have been reported since version 1.3, when 8G was taken out of beta and officially launched last year. Continue reading »
Been getting hit with massive attacks on all sites. Very large VPN/proxy network. Relentless requests 24/7, thousands of requests every minute, just non-stop attacks. All URL requests targeting rogue PHP files. The attacks were weighing on precious server resources. Server held up fine but this nonsense needed to stop. So I wrote a tight little addon for my 8G Firewall. Blocks the entire attack with just a few clicks.. Continue reading »

As a full-time web developer and typical human being, I rely on the Internet for a great many things. So when the Internet is not available, my work (and play) comes to a grinding halt. Fortunately my primary ISP is pretty solid, but it still goes down every once in a while. So to maintain my workflow (and general sanity), having a backup Internet service provider is absolutely essential. Here’s one way to do it.. Continue reading »
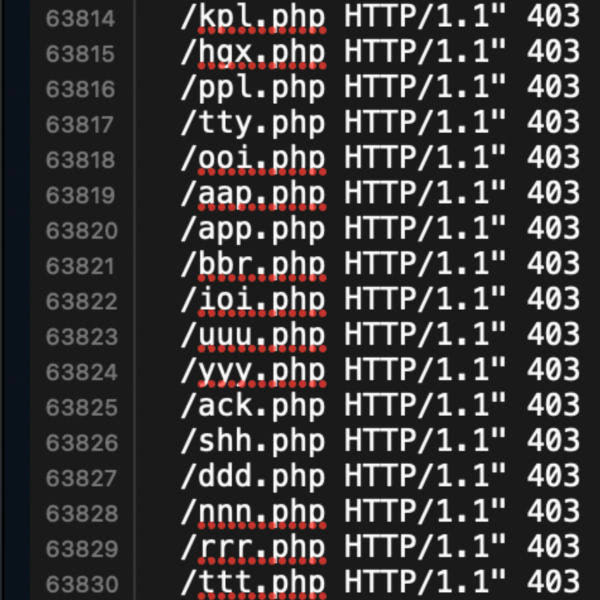
I’ve been working on developing the 8G Firewall. Digging through log files and crunching the data, the big new trend I’m noticing is heavy scanning for easy targets, low hanging fruit. Bad actors are looking for any little hidden files stashed on your server. Mostly PHP files, also ZIP and RAR files, and other file formats commonly used for compressing and archiving content. Basically, anything that might contain useful information (like login credentials, database backups, email addresses, etc.). Also, 99% […] Continue reading »

BBQ Firewall is built to be powerful, lightweight, fast and flexible. It’s code base is kept super lean, leaving extra functionality out of core while supporting new features via simple addons. For example, this tutorial shows how to use an addon to display the total number of blocked HTTP requests on the plugin settings page. This can help you get a basic idea of the plugin’s effectiveness. Continue reading »

This tutorial is for users of my nG Firewall, version 8G or better. It explains how to enable logging for all blocked requests. This is useful for testing, debugging, and keeping an eye on things. Takes only a few minutes to set up, and of course it’s all open source and 100% free for everyone :) Continue reading »

After more than a year of beta testing, 8G Firewall is ready for use on production sites. So you can benefit from the powerful protection provided by the latest evolution of the nG Firewall (aka nG Blacklist). The 8G Firewall offers lightweight, server-level protection against a wide range of malicious requests, bad bots, automated attacks, spam, and many other types of threats and nonsense. 8G is a lightweight (only 17KB) strong firewall that provides site security and peace of mind. […] Continue reading »

The nG Firewall is a carefully crafted set of security rules for Apache and Nginx servers. nG may be applied via your site’s public root .htaccess file, or added via server configuration file. Once added, 8G provides powerful server-level protection against a wide range of malicious requests, bad bots, automated attacks, spam, and many other types of threats and nonsense. It’s a lightweight yet super strong firewall that improves site security and peace of mind. Continue reading »
I use domain-based emails for 99% of my email activity. The other 1% is comprised of assorted 3rd-party email services and temporary slash disposable addresses (like for testing purposes and one-off sign-ups, etc.). I can tell you whole-heartedly based on 20+ years working online that self-hosted email is THE WAY to go. Continue reading »

Like many of you, I have been working online for years now, more than most. Over the course of the past 20 years, I have created accounts at hundreds and hundreds of websites. That includes all the work-related stuff, like web development, plus LOTS of social media sites, online services for everything from email to security monitoring. Not to mention all of the accounts created for mundane things like banking, utilities, Internet and phone service, and so forth. Continue reading »
Your website’s robots.txt file probably contains some rules that tell compliant search engines and other bots which pages they can visit, and which are not allowed, etc. In most of the robots.txt files that I’ve looked at, all of the Allow and Disallow rules are applied to all user agents. This is done with the wildcard operator, which is written as an asterisk *, like this: User-agent: * This site’s robots.txt file provides a typical example. All of the allow/disallow […] Continue reading »

I’ve tried 1Password and Dashlane, and several other popular password managers for both Mac and PC. It always seems to be the same thing: things start off great and then go downhill from there. For example, I was loving 1Password, and then it locked me out of my password file/account. Likewise for a couple of years Dashlane was great, but then they started making drastic changes like moving from standalone app to browser extension Web-based UI. The confusion involved with […] Continue reading »
There are numerous ways to redirect requests using Apache’s mod_rewrite and mod_alias. This concise, friendly tutorial explains different ways to redirect a range of IP addresses, either IPv4 or IPv6. Continue reading »
Let’s say you have some .htaccess rewrite rules in place using Apache’s mod_rewrite. By default if the rewrite rules are located in the root directory, they will be applied to every subdirectory, as expected. But what if you need to disable the rewrite rules so that they do not affect some specific sub-directory or sub-folder? This super quick tutorial shows the easiest way to do it. Continue reading »

After several months of development, the official Nginx version of the 7G Firewall is out of beta and ready for public use. If you are not familiar with 7G Firewall, check out the documentation for the Apache/.htaccess version. The Nginx version of the 7G Firewall works the exact same way, so I won’t bother repeating everything here. The only difference is the implementation, how to set it up on an Nginx server, which is explained in this post. Continue reading »










