
I’ve tried 1Password and Dashlane, and several other popular password managers for both Mac and PC. It always seems to be the same thing: things start off great and then go downhill from there. For example, I was loving 1Password, and then it locked me out of my password file/account. Likewise for a couple of years Dashlane was great, but then they started making drastic changes like moving from standalone app to browser extension Web-based UI. The confusion involved with […] Continue reading »

Have you ever wanted to make a WordPress site private? So that only specific users are allowed access? For example, for my found-images site eChunks.com, I decided to require user login in order to access any content. So now for that site, public access is not allowed, and any posts, images, and all other content is available only to logged-in users. This tutorial explains four ways to make a WordPress site private or members only, so that only authenticated/trusted users […] Continue reading »
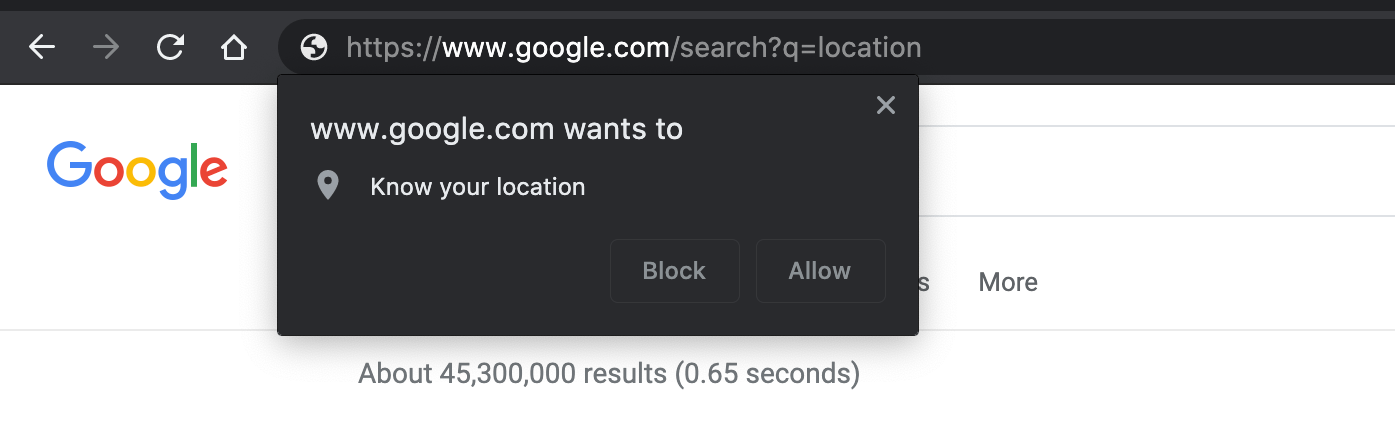
Want to stop Google Chrome browser from constantly asking for permission to “know your location”? This mini tutorial shows how to do it quickly and easily, for Google Chrome versions (around) 83 and better. Continue reading »

This post is a bit different than my regular in-depth tutorials. This is where I scribble down notes and thoughts about my experience switching from Photoshop (PS) to Affinity Photo (AP). As I continue to learn AP and collect more notes, I’ll add them to this post. It’s an informal work in progress. To give some context of where I’m coming from, I have around 20 years experience working with Photoshop (and other Adobe apps). Like many others, for me […] Continue reading »
![[ The Cleaner ]](https://perishablepress.com/wp/wp-content/images/2020/professional-cleaner.jpg)
Zipping files on Apple/Mac is a chore because of all the hidden files and folders added by macOS. Like .DS_Store and __MACOSX are two of the most common files and folders that are added to zip files when compressed on macOS. The folder named __MACOSX especially is problematic because it contains duplicates of every file in the zip archive. So for example, if you use Finder to compress 20 files, the resulting zip file will contain the original 20 files, […] Continue reading »
![[ Screenshot of pathetic Facebook post ]](https://perishablepress.com/wp/wp-content/images/2020/how-to-ask-questions.jpg)
I see so many technical (and other) questions in forums and social media that go unanswered. Not due to lack of trying, but due to lack of understanding. People posting questions like this (an actual post in a popular PHP group on FB): Continue reading »
It is debatable whether or not Chrome’s new scrolltotextfragment feature is a significant security concern. When in doubt, play it safe. This quick post explains how to disable (or enable) Chrome’s scroll-to-text-fragment functionality. Continue reading »
The ones I know of: ads.txt humans.txt robots.txt security.txt This site makes use of robots.txt and humans.txt. I don’t need ads.txt because 3rd-party ads aren’t currently running on the site, and security.txt seems not necessary as the site’s contact form is easy enough for anyone to find. Continue reading »
![[ POST Requests ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-post-requests.jpg)
I’ve written before about protecting against malicious POST requests using Apache/.htaccess. In this tutorial, we’ll look at how to modify GET and POST requests using PHP and some core WordPress functionality (with no .htaccess required). Normally you would want to manipulate URI requests at the server level, but that’s not always possible (like on shared hosting). So in those cases where you want to modify GET, POST, or other types of requests on a WordPress site, check out the following […] Continue reading »
![[ Get Help ]](https://perishablepress.com/wp/wp-content/images/2019/ask-get-help-cat.jpg)
When working online or offline in the real world, it’s inevitable that you will encounter issues and problems with products, services, and everything else. This quick post explains when, where, and how to ask for help: The Three Golden Rules. It’s a general guide, aimed at those who may be unfamiliar. Continue reading »
![[ Monitor WordPress Login Page ]](https://perishablepress.com/wp/wp-content/images/2019/monitor-wordpress-login-page.jpg)
There are all sorts of plugins that you can use to monitor and protect the WordPress Login Page. That’s not what this post is about. This post is aimed at developers and DIY site admins, who like to keep a close eye on site activity. Talking hands-on with code. How familiar are you with the traffic hitting your WP Login Page? Do you know the difference between a brute-force attack and legitimate login requests? The WP Login Page (wp-login.php) is […] Continue reading »
![[ Call to undefined function ]](https://perishablepress.com/wp/wp-content/images/2019/fix-error-undefined.png)
I’m seeing a big increase in bot attacks targeting theme files directly. First they get the URL to your theme directory. There are numerous ways for a bot to get this information. For example most themes include assets like CSS and JavaScript files, and the link includes the full URL. So then once they have the theme URL, bad bots will make direct requests for well-known theme template files, like index.php and header.php. Requesting template files directly may reveal possible […] Continue reading »
![[ WordPress Ultimate Comment Blacklist ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-comment-blacklist.jpg)
How do YOU stop comment spam? If you’re like a lot of WordPress users, you just grab another plugin or two and call it good. I mean after all, plugins like Akismet work great at stopping spam. The only downside is that, well, you’re relying on another plugin. And that’s fine for folks who just wanna “get ’er done”, although each active plugin requires additional maintenance and server resources. Continue reading »
![[ Automatic IP Blacklist ]](https://perishablepress.com/wp/wp-content/images/2018/automatic-ip-address-blacklist.jpg)
Recently a reader going by the name of Rock Star sent me a cool little PHP script that automatically updates your site’s .htaccess with a current list of bad IP addresses. This is useful because it gives you better “real time” protection against attacks and malicious requests. This tutorial shares the code and explains how to implement in two easy steps. Continue reading »
![[ Mr. PHP fsockopen CSF ]](https://perishablepress.com/wp/wp-content/images/2018/mr-php-fsockopen-csf.jpg)
Recently started some sites with Liquid Web hosting, everything going extremely well all around. There was one hiccup (at least for me) where PHP’s fsockopen was not working. At the time, I was trying to figure out why the Whois Lookup feature used by Blackhole Bad Bots was not working. Initial investigation revealed that fsockopen() external HTTP requests were getting blocked somewhere. Everything else worked, including making the requests via cURL. Continue reading »
![[ The circle is now complete. ]](https://perishablepress.com/wp/wp-content/images/2018/circle-now-complete.jpg)
In previous posts, I’ve explained how to verify identity of search engines and other bots, by looking up the host name and then doing a reverse lookup to cross-check the IP address. This is often referred to as a forward-reverse lookup, or something to that effect. The point is, there are plenty of free online tools available for performing forward-reverse IP/host lookups. And online tools are great, but it’s also possible to do forward/reverse lookups directly via the command line, […] Continue reading »





![[ The Cleaner ]](https://perishablepress.com/wp/wp-content/images/2020/professional-cleaner.jpg)
![[ Screenshot of pathetic Facebook post ]](https://perishablepress.com/wp/wp-content/images/2020/how-to-ask-questions.jpg)
![[ POST Requests ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-post-requests.jpg)
![[ Get Help ]](https://perishablepress.com/wp/wp-content/images/2019/ask-get-help-cat.jpg)
![[ Monitor WordPress Login Page ]](https://perishablepress.com/wp/wp-content/images/2019/monitor-wordpress-login-page.jpg)
![[ Call to undefined function ]](https://perishablepress.com/wp/wp-content/images/2019/fix-error-undefined.png)
![[ WordPress Ultimate Comment Blacklist ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-comment-blacklist.jpg)
![[ Automatic IP Blacklist ]](https://perishablepress.com/wp/wp-content/images/2018/automatic-ip-address-blacklist.jpg)
![[ Mr. PHP fsockopen CSF ]](https://perishablepress.com/wp/wp-content/images/2018/mr-php-fsockopen-csf.jpg)
![[ The circle is now complete. ]](https://perishablepress.com/wp/wp-content/images/2018/circle-now-complete.jpg)
