
As a full-time web developer and typical human being, I rely on the Internet for a great many things. So when the Internet is not available, my work (and play) comes to a grinding halt. Fortunately my primary ISP is pretty solid, but it still goes down every once in a while. So to maintain my workflow (and general sanity), having a backup Internet service provider is absolutely essential. Here’s one way to do it.. Continue reading »
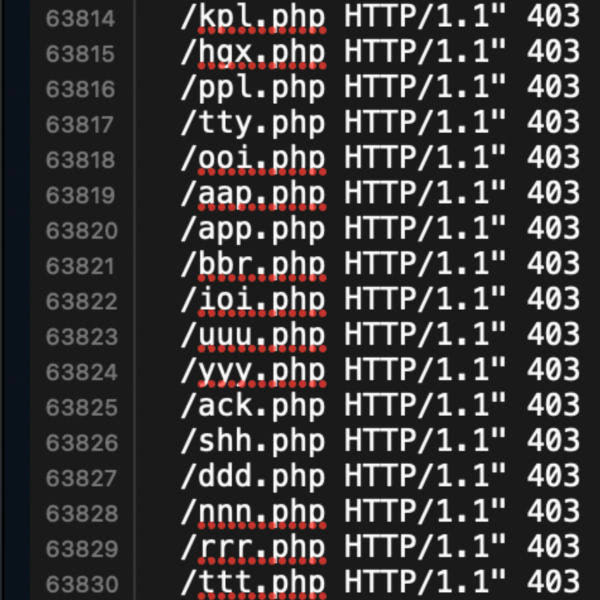
I’ve been working on developing the 8G Firewall. Digging through log files and crunching the data, the big new trend I’m noticing is heavy scanning for easy targets, low hanging fruit. Bad actors are looking for any little hidden files stashed on your server. Mostly PHP files, also ZIP and RAR files, and other file formats commonly used for compressing and archiving content. Basically, anything that might contain useful information (like login credentials, database backups, email addresses, etc.). Also, 99% […] Continue reading »
I use domain-based emails for 99% of my email activity. The other 1% is comprised of assorted 3rd-party email services and temporary slash disposable addresses (like for testing purposes and one-off sign-ups, etc.). I can tell you whole-heartedly based on 20+ years working online that self-hosted email is THE WAY to go. Continue reading »

There are many free (and commercial) uptime monitoring services that will alert you if your server goes offline. These services are popular because it’s mission critical to know when your sites are down. The sooner you know about it, the sooner you can scramble to get everything back online. I’ve tried other scripts and services but nothing that met my specific needs: simple, secure, lightweight and blazing fast. So decided roll my own DIY server status monitor and share it […] Continue reading »

Like many of you, I have been working online for years now, more than most. Over the course of the past 20 years, I have created accounts at hundreds and hundreds of websites. That includes all the work-related stuff, like web development, plus LOTS of social media sites, online services for everything from email to security monitoring. Not to mention all of the accounts created for mundane things like banking, utilities, Internet and phone service, and so forth. Continue reading »
Your website’s robots.txt file probably contains some rules that tell compliant search engines and other bots which pages they can visit, and which are not allowed, etc. In most of the robots.txt files that I’ve looked at, all of the Allow and Disallow rules are applied to all user agents. This is done with the wildcard operator, which is written as an asterisk *, like this: User-agent: * This site’s robots.txt file provides a typical example. All of the allow/disallow […] Continue reading »
For years, I’ve not used ModSecurity for any of my own sites. Way back when I first tried ModSecurity, there were just too many false positives, so I stayed away from it, opting instead to develop my own fast Apache/.htaccess firewall. But my web host now is telling me that ModSecurity is required on all of their managed VPS plans. Continue reading »

I’ve tried 1Password and Dashlane, and several other popular password managers for both Mac and PC. It always seems to be the same thing: things start off great and then go downhill from there. For example, I was loving 1Password, and then it locked me out of my password file/account. Likewise for a couple of years Dashlane was great, but then they started making drastic changes like moving from standalone app to browser extension Web-based UI. The confusion involved with […] Continue reading »
There are numerous ways to redirect requests using Apache’s mod_rewrite and mod_alias. This concise, friendly tutorial explains different ways to redirect a range of IP addresses, either IPv4 or IPv6. Continue reading »
Let’s say you have some .htaccess rewrite rules in place using Apache’s mod_rewrite. By default if the rewrite rules are located in the root directory, they will be applied to every subdirectory, as expected. But what if you need to disable the rewrite rules so that they do not affect some specific sub-directory or sub-folder? This super quick tutorial shows the easiest way to do it. Continue reading »

Have you ever wanted to make a WordPress site private? So that only specific users are allowed access? For example, for my found-images site eChunks.com, I decided to require user login in order to access any content. So now for that site, public access is not allowed, and any posts, images, and all other content is available only to logged-in users. This tutorial explains four ways to make a WordPress site private or members only, so that only authenticated/trusted users […] Continue reading »
It is debatable whether or not Chrome’s new scrolltotextfragment feature is a significant security concern. When in doubt, play it safe. This quick post explains how to disable (or enable) Chrome’s scroll-to-text-fragment functionality. Continue reading »
![[ POST Requests ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-post-requests.jpg)
I’ve written before about protecting against malicious POST requests using Apache/.htaccess. In this tutorial, we’ll look at how to modify GET and POST requests using PHP and some core WordPress functionality (with no .htaccess required). Normally you would want to manipulate URI requests at the server level, but that’s not always possible (like on shared hosting). So in those cases where you want to modify GET, POST, or other types of requests on a WordPress site, check out the following […] Continue reading »
![[ Prevent WordPress Automatic .htaccess Modifications ]](https://perishablepress.com/wp/wp-content/images/2016/wordpress-htaccess.jpg)
In a recent tutorial, I explain how to Stop WordPress from modifying .htaccess. That post explains several ways to prevent WordPress from making changes to .htaccess. This post explains an even better way that is safe, effective, non-invasive, re-usable, and super simple. I’ve been using it on my own sites now for a few years and it works flawlessly. Continue reading »
![[ Monitor WordPress Login Page ]](https://perishablepress.com/wp/wp-content/images/2019/monitor-wordpress-login-page.jpg)
There are all sorts of plugins that you can use to monitor and protect the WordPress Login Page. That’s not what this post is about. This post is aimed at developers and DIY site admins, who like to keep a close eye on site activity. Talking hands-on with code. How familiar are you with the traffic hitting your WP Login Page? Do you know the difference between a brute-force attack and legitimate login requests? The WP Login Page (wp-login.php) is […] Continue reading »
Finally put together a giant list of .htaccess redirect examples. It’s meant as a quick copy-&-paste resource for those who may be looking for an assortment of redirect techniques. Here you will find redirects via mod_alias and mod_rewrite. Examples include redirecting to and from any directory, subdirectory, resource, URL, and much more. Most of these examples are taken from my previous article, Stupid htaccess Tricks; other examples are taken from previous .htaccess tutorials here at Perishable Press. Enjoy! :) Continue reading »








![[ POST Requests ]](https://perishablepress.com/wp/wp-content/images/2019/wordpress-post-requests.jpg)
![[ Prevent WordPress Automatic .htaccess Modifications ]](https://perishablepress.com/wp/wp-content/images/2016/wordpress-htaccess.jpg)
![[ Monitor WordPress Login Page ]](https://perishablepress.com/wp/wp-content/images/2019/monitor-wordpress-login-page.jpg)
