Examples of Email Phishing in 2024
 I enjoy sharing the pathetic phishing emails that make it past my spam filters. After watching various waves of phishing campaigns come and go over the past 20 years, I have come to accept that it’s just a part of life on the Web. Phishing scams have been happening since the dawn of the Internet, with no signs of stopping anytime soon. About the best you can do is practice safe email handling practices and never open any links or respond to any messages that you don’t recognize and/or look shady or questionable in general. This post aims to help by sharing some examples of phishing attempts, along with a breakdown of red flags and ways to identify bogus email.
I enjoy sharing the pathetic phishing emails that make it past my spam filters. After watching various waves of phishing campaigns come and go over the past 20 years, I have come to accept that it’s just a part of life on the Web. Phishing scams have been happening since the dawn of the Internet, with no signs of stopping anytime soon. About the best you can do is practice safe email handling practices and never open any links or respond to any messages that you don’t recognize and/or look shady or questionable in general. This post aims to help by sharing some examples of phishing attempts, along with a breakdown of red flags and ways to identify bogus email.
Contents
- Basic Strategy
- Phishing Email #1
- Phishing Email #2
- Phishing Email #3
- Phishing Email #4
- Phishing Email #5
- More Phishing Examples
- Wrap Up
Basic Strategy
When trying to decide if an email or any other correspondence is legitimate, err on the side of caution and assume it’s fake. Don’t click on anything, load any images, hover over any links, or respond in any way. This is my basic strategy and it’s been working great for many years with solid track record.
To confirm that an email is bogus, examine the details. That’s where the phishers always fall short. Phishing emails usually are loaded with all sorts of little stupid errors. The more you look, the more mistakes you’ll find. To help illustrate, here are some recent examples of email phishing attempts..
Phishing Email #1
💩 What it looks like:
💩 What it says (in plain text):
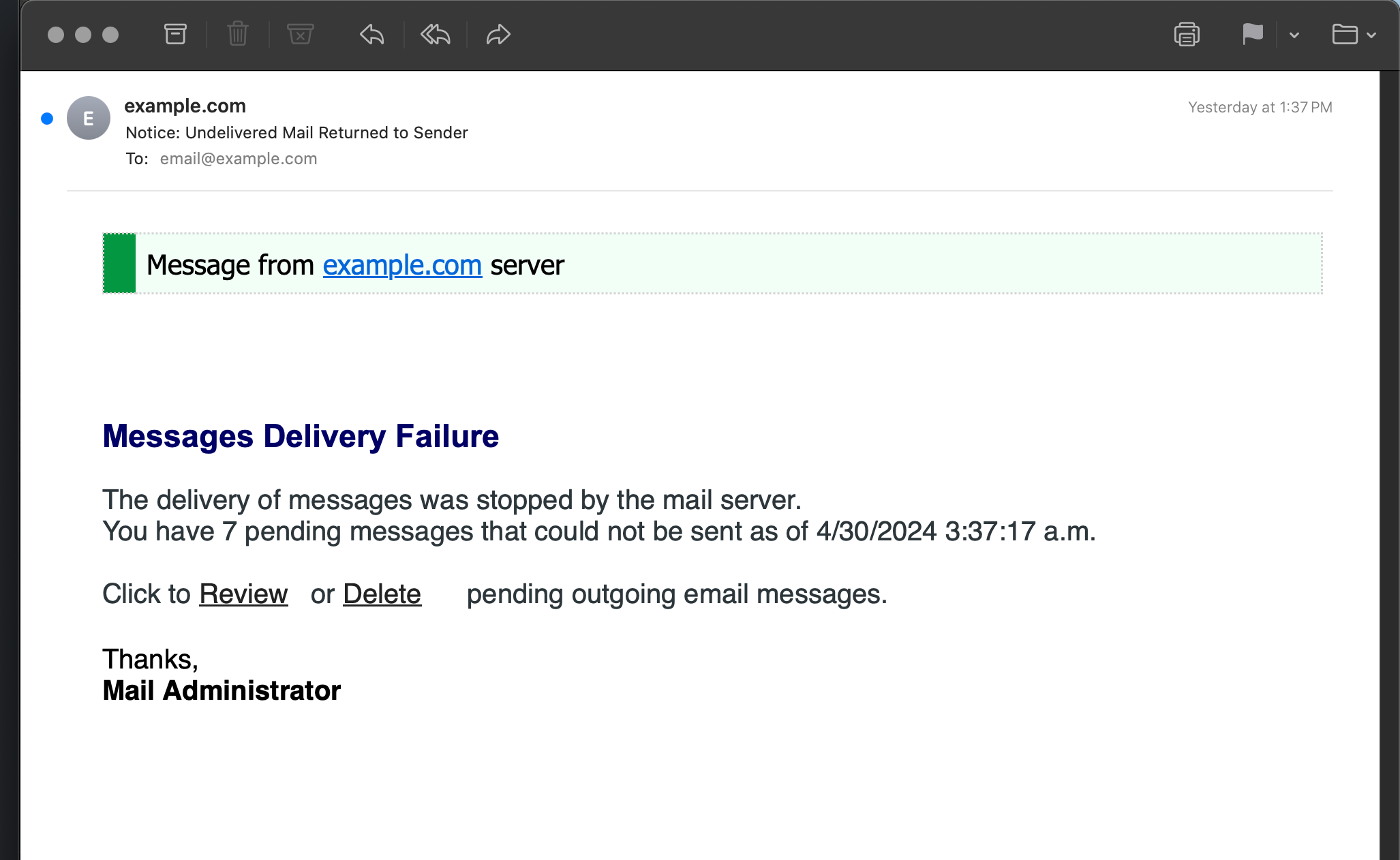
Notice: Undelivered Mail Returned to Sender
Message from example.com server
Messages Delivery Failure
The delivery of messages was stopped by the mail server.
You have 7 pending messages that could not be sent as of 4/30/2024 3:37:17 a.m.
Click to Review or Delete pending outgoing email messages.
Thanks,
Mail Administrator💩 What this really is: A weak attempt at stealing your password and gain entry to your email account and/or server.
💩 How to tell it’s fake:
- Sender is not recognized
- Weird whitespace between words
- Weird vertical space between sentences
- Grammar mistakes like “Messages Delivery”
- Signed as “Thanks, Mail Administrator” lol
- And why is “Mail Administrator” in bold text?
This phishing example is better crafted than the others. It is short and to the point with not too many mistakes. Even so, examining the details reveals this email as fake. And beyond the obvious up-front signs, if you dig a bit into the source code there are many more tells that it’s a (rather sad) attempt at stealing your passwords or worse.
Phishing Email #2
💩 What it looks like:
💩 What it says (in plain text):
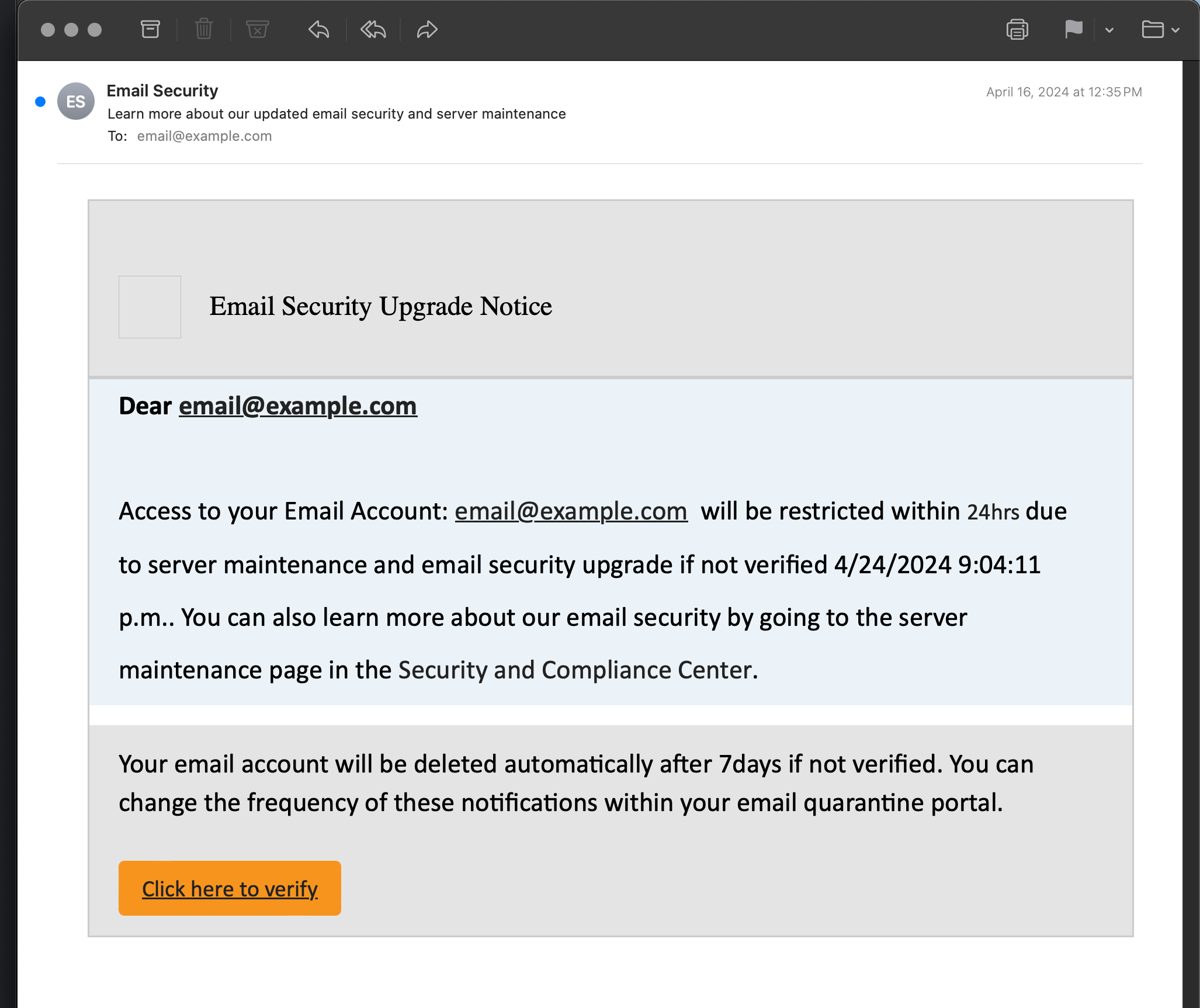
Email Security
Learn more about our updated email security and server maintenance
Email Security Upgrade Notice
Dear email@example.com
Access to your Email Account: email@example.com will be restricted within 24hrs due to server maintenance and email security upgrade if not verified 4/24/2024 9:04:11 p.m.. You can also learn more about our email security by going to the server maintenance page in the Security and Compliance Center.
Your email account will be deleted automatically after 7days if not verified.
You can change the frequency of these notifications within your email quarantine portal.
Click here to verify💩 What this really is: A weak attempt at stealing your password and gain entry to your email account and/or server.
💩 How to tell it’s fake:
- Message is from “Email Security”, whatever that is
- “Email Security Upgrade Notice” just sounds totally fake
- The greeting is a hyperlinked email address instead of plain-text name
- The premise/logic of the email is completely bizarro-world
- Grammar/spelling issues (e.g., no space between “7days”)
- Sorry but “Email quarantine portal” also sounds fake
- The “Click here to verify” hyperlinked button
This is another halfway passable phishing attempt. Relatively short and to the point, even though the point is plain ridiculous. A few minor mistakes and subtle weirdness, that’s all. I would bet emails like this “catch” a lot of people off guard. They quickly scan the message, something about “security”, “maintenance”, and “verify”.. so they click on the big orange button to take care of it. The next thing you know, they’re digital wrestling with some unscrupulous louse trying to take advantage.
Phishing Email #3
💩 What it looks like:
💩 What it says (in plain text):
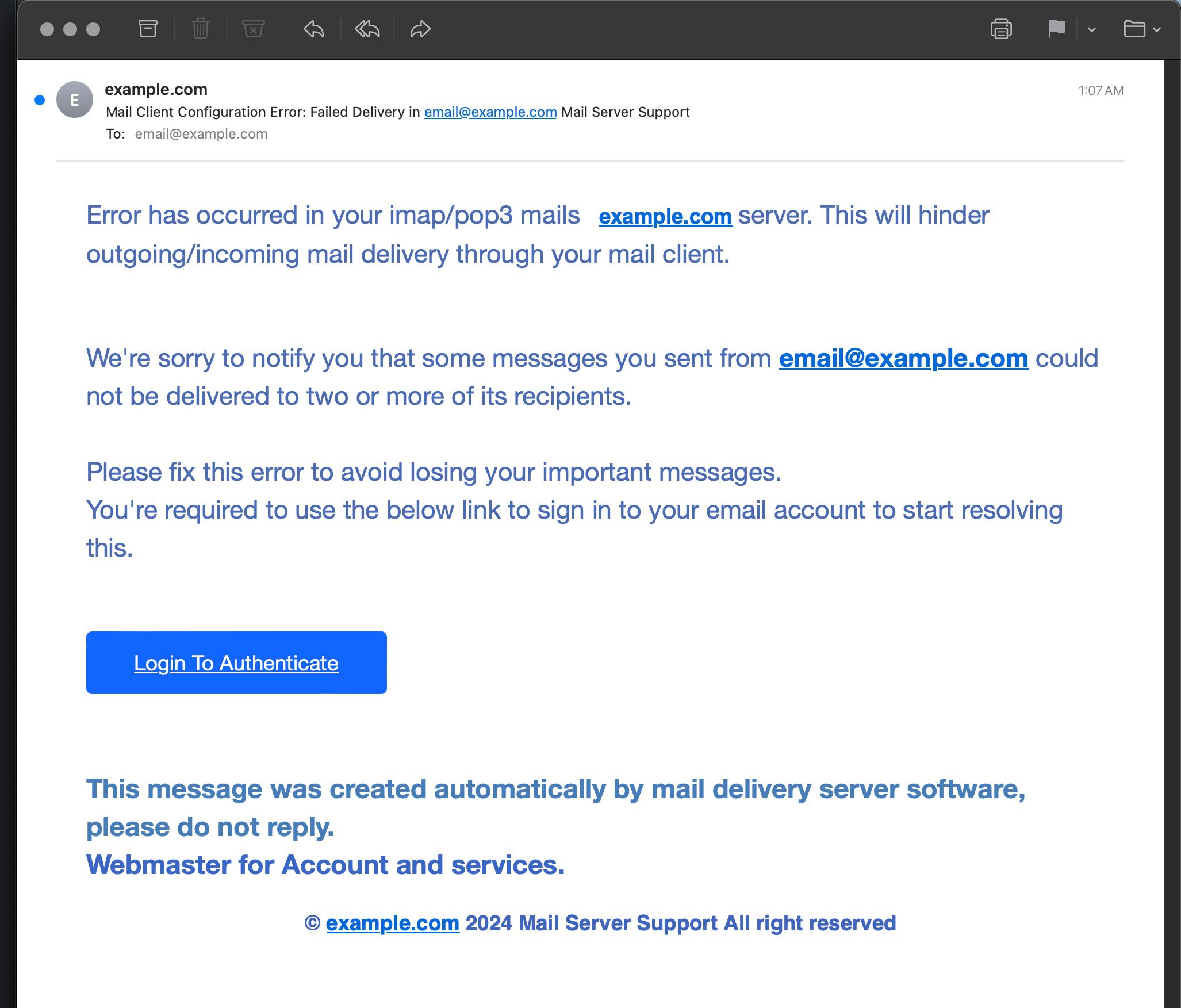
Mail Client Configuration Error: Failed Delivery in email@example.com Mail Server Support
Error has occurred in your imap/pop3 mails example.com server. This will hinder outgoing/incoming mail delivery through your mail client.
We're sorry to notify you that some messages you sent from email@example.com could not be delivered to two or more of its recipients.
Please fix this error to avoid losing your important messages.
You're required to use the below link to sign in to your email account to start resolving this.
Login To Authenticate
This message was created automatically by mail delivery server software, please do not reply.
Webmaster for Account and services.
© example.com 2024 Mail Server Support All right reserved💩 What this really is: A weak attempt at stealing your password and gain entry to your email account and/or server.
💩 How to tell it’s fake:
- Weird gap between words in first sentence
- No opening/welcome line, just jumps right in
- Incorrect lowercase spelling of “imap” and “pop3”
- Inconsistent vertical spacing between paragraphs and buttons
- Why would only “important” messages be lost, why not all messages
- Third paragraph broken with needless line break after first sentence
- The sentence before the button sounds like it was written by a 3rd-grader
- “You’re required to use the below link” uh-huh, yeah OK
- “To start resolving this”, is just a dead giveaway
- The “Login To Authenticate” underlined hyperlinked button
- The heavy handed bold footer text screams “fake”
This phishing email might catch a lot of people off-guard due its relatively uniform simplicity. But even just a few moments examining the details reveals its true pathetic nature. Only at first blink would this email seem legit. Three different shades of blue for a “configuration error” email alert is pretty obvious. Plus heavy bold font choice for three lines of footer text, screams “we’re trying so hard to look legitimate”.
Phishing Email #4
💩 What it looks like:
💩 What it says (in plain text):
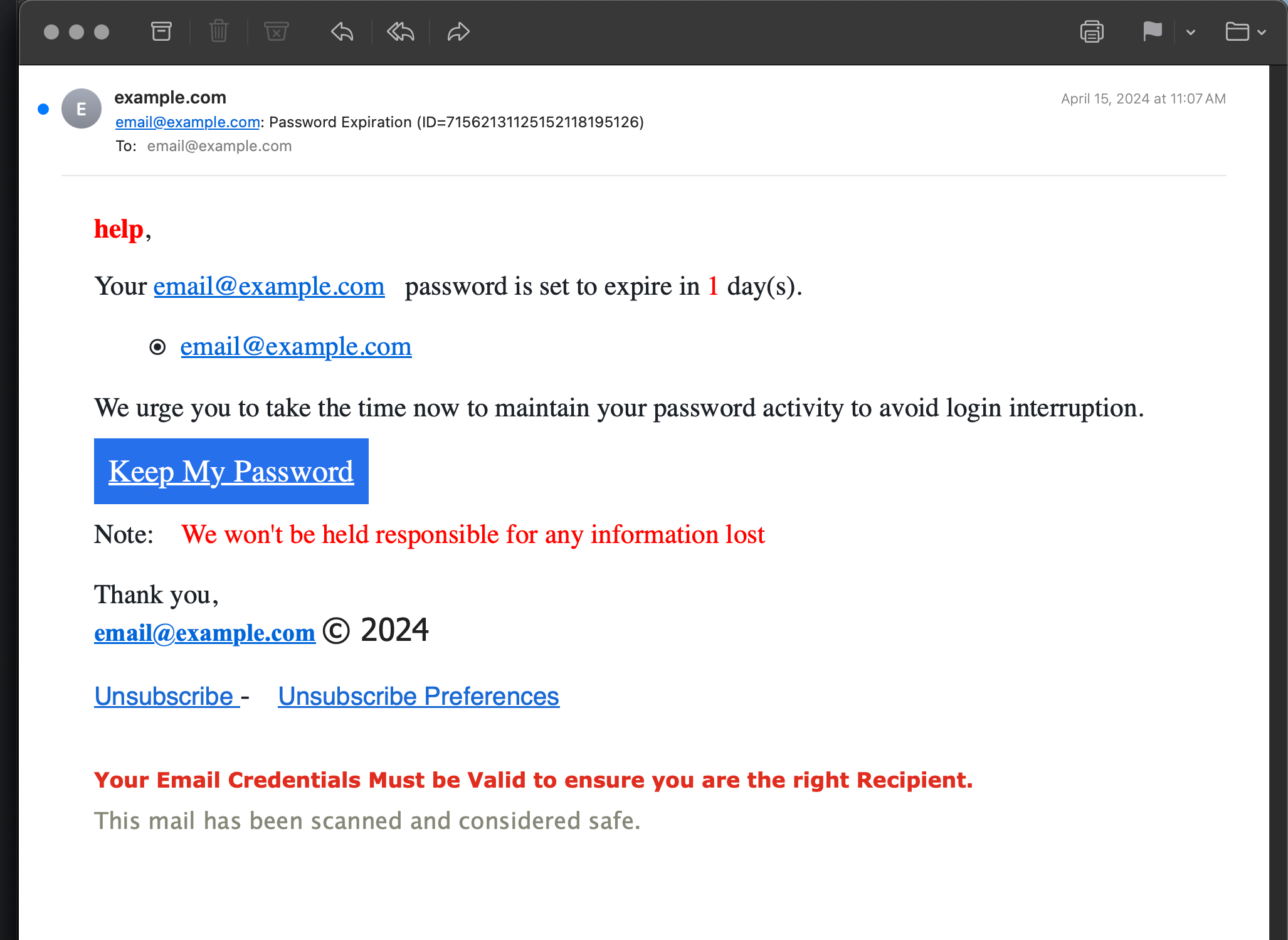
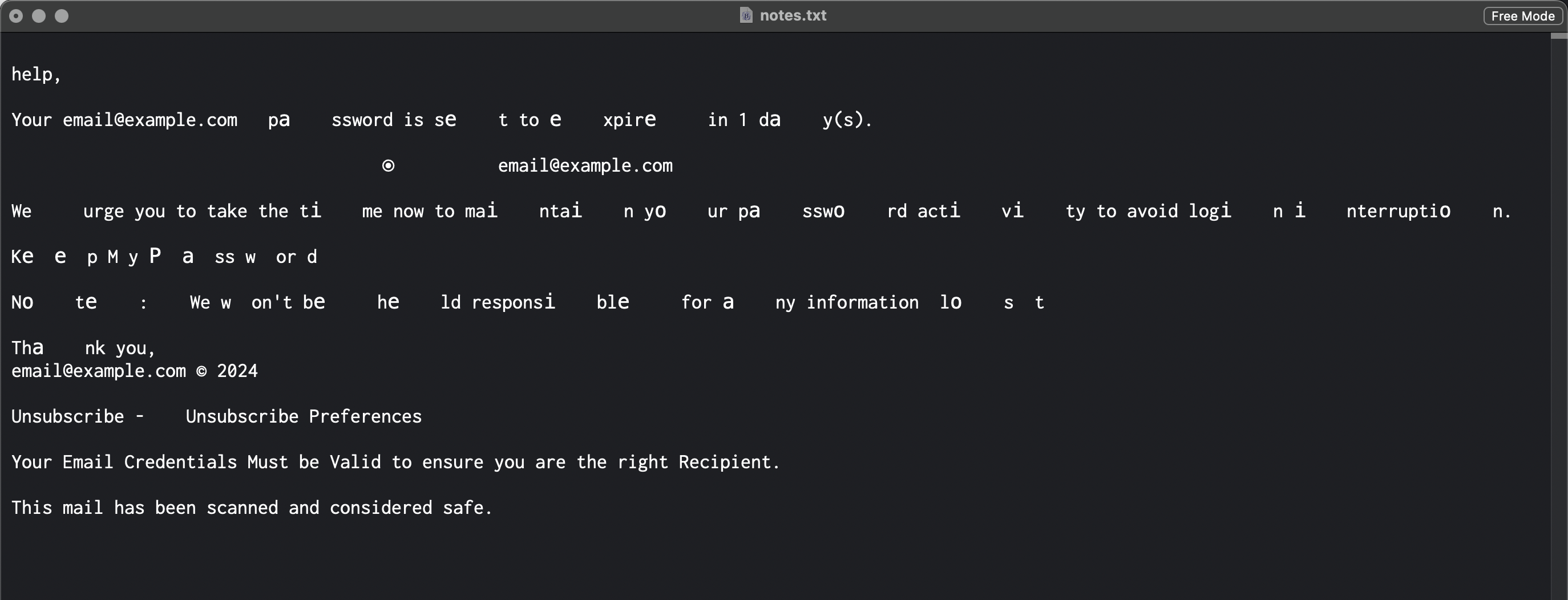
email@example.com: Password Expiration (ID=71562131125152118195126)
help,
Your email@example.com password is set to expire in 1 day(s).
* email@example.com
We urge you to take the time now to maintain your password activity to avoid login interruption.
Keep My Password
Note: We won't be held responsible for any information lost
Thank you,
email@example.com (c) 2024
Unsubscribe - Unscribe Preferences
Your Email Credentials Must be Valid to ensure you are the right Recipient.
This mail has been scanned and considered safe.💩 What this really is: A weak attempt at stealing your password and gain entry to your email account and/or server.
💩 How to tell it’s fake:
- Sender is not recognized
- Message is addressed to “help” lol
- Weird inconsistent spacing between words
- How do you even “maintain your password activity”
- The giant desperate blue button that says “Keep My Password”
- The note that says “We won’t be held responsible for any information lost”
- The signature was my email address, not the sender’s
- The giant copyright date
- Penultimate sentence is ridiculous
Additionally, the message content is obfuscated to help bypass anti-spam filters. You can tell easily by copy/pasting the email message into a text editor that can display rich text. To illustrate, here is what the above message text looks like when displayed using BBEdit text editor. Click image to view full-size (opens new tab).
Notice the missing/replaced characters mixed in with regular text. Because of all the encoded characters, symbols, and other shenanigans, the email message looks (and is) broken when interpreted as actual text.
Phishing Email #5
💩 What it looks like:
💩 What it says (in plain text):
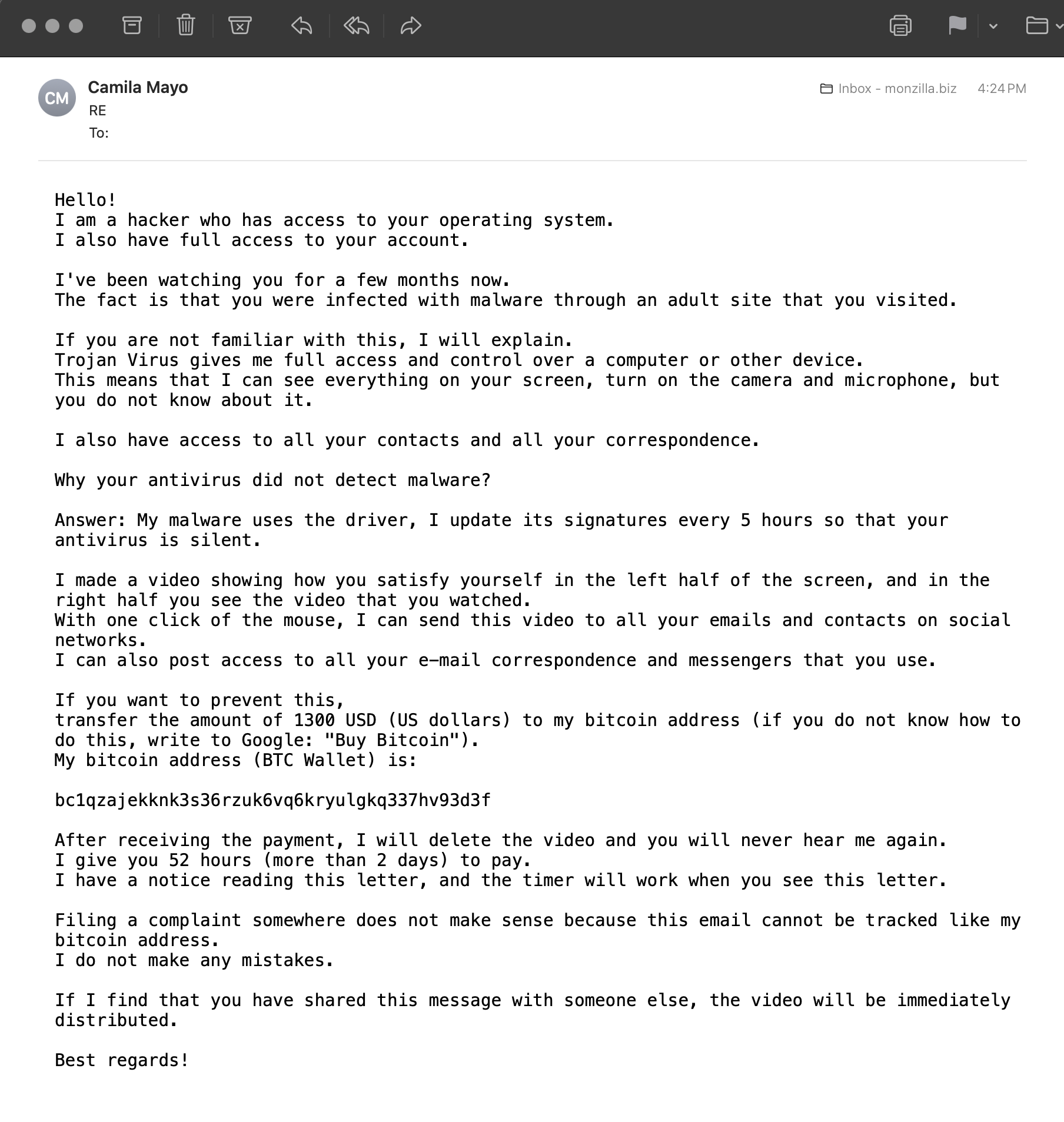
Hello!
I am a hаckеr who has аccess to your operating system.
I also have full аccess to your account.
I've been wаtching you for a few months now.
The fact is that you were infected with malwаre through an аdult site that you visited.
If you are not familiar with this, I will explain.
Trojаn Virus gives me full аccess and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
I also have аccess to all your contacts and all your correspondence.
Why your аntivirus did not detect mаlwаre?
Answеr: My mаlwаre uses the driver, I update its signatures every 5 hours so that your аntivirus is silent.
I made a vidеo showing how you sаtisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this vidеo to all your emаils and contacts on social networks.
I can also post access to all your e-mail corrеspondence and mеssengers that you use.
If you want to prevent this,
trаnsfer the аmount of 1300 USD (US dollаrs) to my bitcоin аddress (if you do not know how to do this, write to Google: "Buy Bitcоin").
My bitcоin address (ВТС Wallet) is:
1234567890abcdefghijklmnopqrstuvwxyz
After receiving the pаyment, I will delеte the vidеo and you will never hear me again.
I give you 52 hоurs (more than 2 days) to pаy.
I have a notice reading this lеtter, and the timer will work when you see this letter.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitсоin аddrеss.
I do not make any mistakes.
If I find that you have shared this message with someone else, the video will be immеdiately distributed.
Best regards!💩 What this really is: Psychological manipulation, phishing for any sort of response. Then your name/email/address/info goes on a list for future harassment and scams. Do victims actually send these guys bitcoins? Maybe. But they’re more interested in finding people who react quickly and without thinking, perhaps by simply replying “F*** YOU” to their idiotic drivel, you have taken the bait and fallen into their trap. Never click on, or interact with any email you do not recognize. Just DELETE it and move on.
💩 How to tell it’s fake:
- Message is sent from some anonymous creep
- Tone of the email is adolescent and desperate at best
- Typical basic mistakes with spelling, grammar, syntax, etc.
- It’s a well-known phishing tactic, along with variations like “well hello my perverted friend” and so forth
These types of “gotcha” phishing emails have been around since at least 2010, probably even earlier. So they are very well-known and likely ignored by most folks. This type of email is so common that it has to disguise characters of certain phrases like “I am a hаckеr”, just to make it past all the email spam filters.
To make it past email filters, typical phishing phrases such as “I am a hаckеr” are spelled with Cyrillic characters replacing certain Latin characters. To get a better idea, go ahead and copy “I am a hаckеr” from the phishing email above and enter it into this free tool that identifies unicode characters. Doing so, we get this for the word “hаckеr”:
U+0068 : LATIN SMALL LETTER H
U+0430 : CYRILLIC SMALL LETTER A
U+0063 : LATIN SMALL LETTER C
U+006B : LATIN SMALL LETTER K
U+0435 : CYRILLIC SMALL LETTER IE
U+0072 : LATIN SMALL LETTER RSo they replaced the letters “a” and “e” with their Cyrillic look-alikes. Here is the small letter “a” in Latin: a. And here is the small letter “a” in Cyrillic: а. They look almost identical. So when they write “I am a hаckеr” using Cyrillic letters for “a” and “e”, it changes the pattern and bypasses email filters. Many of the words in the above phishing email have letters replaced.
More Phishing Examples
I could easily spend the next four months analyzing and documenting phishing attempts. But time is short and there are many phishing examples to discuss. So I’ll forgo further expose and just share the remaining phishing examples with just some simple comments. I hope these are useful or at least mildly entertaining. Enjoy!
Phishing Email #6
This example is phishing attempt that targets McAfee users. Dead giveaways include the undefined $receipt_no variable in the opening lines (lol). This is an example of another “shock-and-awe” phishing attempt: they hit you with a large charge amount like $450 or whatever. Enough to make McAfee users take action without thinking.
Phishing Email #7
Same as the previous, here is a variation on McAfee phishing. Besides various grammar and syntax errors, the email header “To address” and “From name” make this phishing attempt pretty easy to spot. Why? Because the “From name” is written in some foreign language that clearly is not English like the rest of the message. And for the “To address”, no legitimate business sends out order receipts to “undisclosed-recipients:;” LOL.
Phishing Email #8
There are these things in language called idioms, common phrases said/written in specific ways that are familiar to native speakers. When it comes to spotting fake emails, idioms are your best friend, along with other linguistic fundamentals like grammar and spelling. For example read the subject line in this rather anemic phishing attempt. Then enjoy a chuckle at the message itself, which is elegant in its simplicity, but painfully obvious when the words are read out loud.
Phishing Email #9
This phishing email uses SUPER LARGE FONT SIZES jumbled together with really tiny font sizes, which makes it suspicious at first glance. This is another “shock-and-awe” type phishing attempt, where they hit you with some ridiculous amount of money that you supposedly are spending, have spent, and/or will spend. Like $896.00 in this example, which apparently has been charged to your PayPal account. Again, the goal with this kind of bait is to get any kind of response from the victim. Whether that’s clicking the dead-giveaway giant blue button or replying to the email in sheer and utter panic.
Phishing Emails 10 & 11
Examples 10 and 11 are variations on a “Norton LifeLock” phishing email. They show that the phishing geniuses are experimenting with different terminology, phrasing, and message content. The overall gist of the scam is the same — large purchase renewing — but the details vary between the two. I would imagine there are numerous variations out there. Likely these particular scammers are keeping track of which ones work best. Note that both emails contain obvious errors in the salutation. And both really punch the hook, like they’re literally screaming at you to call the giant bold blue and white phone number lol.
Phishing Emails 12, 13, 14
Examples 12, 13, and 14 are variations on a “PayPal purchase” phishing email. As with the previous Norton LifeLock emails, these three PayPal examples apparently are variations on the “you made a large PayPal purchase” theme. And talk about variation. Even though the message basically is the same, every detail varies wildly from one to another. The font sizes, font weights, PayPal logo, phone numbers, text alignment, colors, spacing, casing, and everything else. Amazing because these three emails were sent just a few days apart, apparently from the same phishing operation. So either they’re sophisticated enough to keep track of nth-degree permutations. Or they’re simply not competent enough to be consistent.
- View screenshot of Phishing Email #12
- View screenshot of Phishing Email #13
- View screenshot of Phishing Email #14
Wrap Up
Hopefully this article is useful for anyone out there who may not be familiar with email phishing, maybe never received one, or maybe researching some gross email that showed up in your inbox. Remember: if it’s not from someone you know and trust, mark as spam and delete it.



One response to “Examples of Email Phishing in 2024”
I almost fell for one of those phishing emails because I trusted a simple input text as a honeypot. They are getting quite clever.