I’ve written before about how to protect WordPress XML-RPC and why it’s important. In this quick post, I explain three easy ways to to disable WordPress XML-RPC to help improve the security of your WordPress-powered site. Continue reading »
![[ _blank Target Vulnerability ]](https://perishablepress.com/wp/wp-content/images/2019/blank-target-vulnerability.jpg)
In this article, I am reposting part of my recent tutorial, WordPress and the Blank Target Vulnerability. That post is aimed at WordPress specifically, however most of the article applies to HTML in general. So the tutorial below explains how to fix all “blank target” links, regardless of whether or not WordPress is involved. Continue reading »
![[ Stormtroopers Keeping Things Secure. ]](https://perishablepress.com/wp/wp-content/images/2019/security-obscurity.jpg)
ob·scure adjective 1. not discovered or known about; uncertain. In the purely literal sense, the concept of obscurity applies to every transaction on the Web. The HTTP request knows not, nor could possibly know, the actual response it will receive from the server. There is only expected response. Online nothing is certain until it is. Continue reading »
![[ Automatic IP Blacklist ]](https://perishablepress.com/wp/wp-content/images/2018/automatic-ip-address-blacklist.jpg)
Recently a reader going by the name of Rock Star sent me a cool little PHP script that automatically updates your site’s .htaccess with a current list of bad IP addresses. This is useful because it gives you better “real time” protection against attacks and malicious requests. This tutorial shares the code and explains how to implement in two easy steps. Continue reading »
![[ WP Visual/RTE Insert Link Dialog ]](https://perishablepress.com/wp/wp-content/images/2018/wp-rte-insert-link.png)
For those who haven’t yet noticed, WordPress now adds rel="noopener" attributes for any external links added via the link Quicktag in the Visual/RTE. So if you enable the option, “Open link in a new tab”, WordPress automatically will add the rel noopener attribute to the link. This is to protect against CORS and other exploits that take advantage of blank-target links. It’s a smart move that may escape many in the WordPress community. So in an effort to help foster […] Continue reading »
![[ Watch Cyber Attacks Online ]](https://perishablepress.com/wp/wp-content/images/2017/cyber-threat-map.jpg)
Taking a quick break to watch cyber attacks happening in real time. Continue reading »
Typically malicious scans use some sort of encoding to obscure their payloads. For example, instead of injecting a literal script, the attacker will run it through a PHP encoding function such as base64_encode(), utf8_encode(), or urlencode(). So if and when you need to decode some discovered payload, you can use whichever decoding function will do the job. For example, base64_decode(), utf8_decode(), or urldecode(). Sounds straightforward, but let’s dig a little deeper.. Continue reading »
It seems the WordPress xmlrpc.php file is the target of another type of attack. Before, it was the XML-RPC Pingback Vulnerability. Now, it is the Brute Force Amplification Attack. This post explains what you need to know and then cuts to the chase with several ways to protect your site against this new malicious exploit, as well as all other related threats. Continue reading »
It was recently reported about a WordPress Pingback Vulnerability, whereby an attacker has four potential ways to cause harm via xmlrpc.php, which is the file included in WordPress for XML-RPC Support (e.g., “pingbacks”). In this post, I offer a simple .htaccess technique to lock things down and protect against any meddling via the xmlrpc.php file. Continue reading »
![[ Prise de la Bastille, by Jean-Pierre-Louis-Laurent Houel (Detail) ]](https://perishablepress.com/wp/wp-content/images/2012/tale-hacked-website.jpg)
I love a good story. Almost as much as I enjoy securing websites. Put them together and you’ve got suspense, intrigue, and plenty of encoded gibberish. But no happy ending this time, in this case the smartest decision was to “pull it” and rebuild. The site was just wasted — completely riddled with malicious code. Without current backup data, it would’ve been “game over” for the site, and possibly the business. Continue reading »
![[ Screenshot: malicious iframe injected into web page ]](https://perishablepress.com/wp/wp-content/images/2012/video-player-swfobject.gif)
During the recent redesign, I discovered that my newer WP installation (v3.3.1) had been hacked. I get this email first thing in the morning: Continue reading »

Awhile ago, Silvan Mühlemann conducted a 1.5 year experiment whereby different approaches to email obfuscation were tested for effectiveness. Nine different methods were implemented, with each test account receiving anywhere from 1800 to zero spam emails. Here is an excerpt from the article: When displaying an e-mail address on a website you obviously want to obfuscate it to avoid it getting harvested by spammers. But which obfuscation method is the best one? I drove a test to find out. After […] Continue reading »
![[ #1 ]](https://perishablepress.com/wp/wp-content/images/2009/eight-blacklist/01.gif)
With the imminent release of the next series of (4G) blacklist articles here at Perishable Press, now is the perfect time to examine eight of the most commonly employed blacklisting methods achieved with Apache’s incredible rewrite module, mod_rewrite. In addition to facilitating site security, the techniques presented in this article will improve your understanding of the different rewrite methods available with Apache mod_rewrite. Note: I changed the title of this post from “Eight Ways to Blacklist..” to “Eight Ways to […] Continue reading »
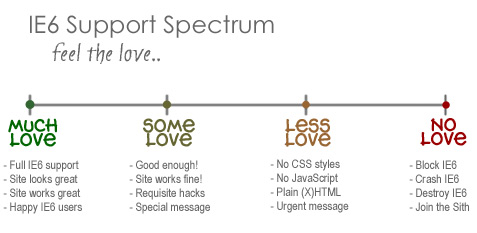
I know, I know, not another post about IE6! I actually typed this up a couple of weeks ago while immersed in my site redesign project. I had recently decided that I would no longer support that terrible browser, and this tangential post just kind of “fell out.” I wasn’t sure whether or not to post it, but I recently decided to purge my draft stash by posting everything for your reading pleasure. Thus, you may see a few turds […] Continue reading »
![[ Content Negotiation ]](https://perishablepress.com/wp/wp-content/images/2008/misc-chunks/content-negotiation.jpg)
In this article, I discuss the different MIME types available for XHTML and explain a method for serving your documents with the optimal MIME type, depending on the capacity of the user agent. Using either htaccess or PHP for content negotiation, we can serve complete, standards-compliant markup for our document’s header information. This is especially helpful when dealing with Internet Explorer while serving a DOCTYPE of XHTML 1.1 along with the recommended XML declaration. According to the RFC standards1 produced […] Continue reading »
![Behold the power of ultimate blacklist! [ Image: Death-metal rocker drunk with power ]](https://perishablepress.com/wp/wp-content/images/2007/misc-chunks/ultimate-nofollow-blacklist.jpg)
Several days ago, I posted an article explaining how to hack your own WordPress nofollow blacklist. Immediately thereafter, I published an elaborate article focusing on automatic methods of nofollow blacklisting via WordPress plugins. In this article, I expand on the original blacklist hack by incorporating functional differentiation between commentator links, trackbacks, and pingbacks. If anything, think of this as an exercise in hacking WordPress, rewarding in and of itself, if not otherwise entirely impractical. Of course, whenever possible, you should […] Continue reading »

![[ _blank Target Vulnerability ]](https://perishablepress.com/wp/wp-content/images/2019/blank-target-vulnerability.jpg)
![[ Stormtroopers Keeping Things Secure. ]](https://perishablepress.com/wp/wp-content/images/2019/security-obscurity.jpg)
![[ Automatic IP Blacklist ]](https://perishablepress.com/wp/wp-content/images/2018/automatic-ip-address-blacklist.jpg)
![[ WP Visual/RTE Insert Link Dialog ]](https://perishablepress.com/wp/wp-content/images/2018/wp-rte-insert-link.png)
![[ Watch Cyber Attacks Online ]](https://perishablepress.com/wp/wp-content/images/2017/cyber-threat-map.jpg)
![[ Prise de la Bastille, by Jean-Pierre-Louis-Laurent Houel (Detail) ]](https://perishablepress.com/wp/wp-content/images/2012/tale-hacked-website.jpg)
![[ Screenshot: malicious iframe injected into web page ]](https://perishablepress.com/wp/wp-content/images/2012/video-player-swfobject.gif)

![[ #1 ]](https://perishablepress.com/wp/wp-content/images/2009/eight-blacklist/01.gif)

![[ Content Negotiation ]](https://perishablepress.com/wp/wp-content/images/2008/misc-chunks/content-negotiation.jpg)
![Behold the power of ultimate blacklist! [ Image: Death-metal rocker drunk with power ]](https://perishablepress.com/wp/wp-content/images/2007/misc-chunks/ultimate-nofollow-blacklist.jpg)
